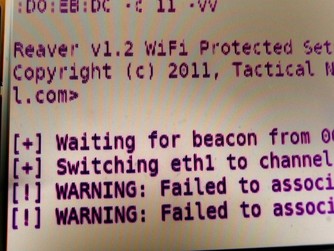
This is really a bullshit . I have 2 ALFA AWUS036H adapters but none of them works with reaver . It stucks on " Waiting for beacon from bssid " and then after sometimes " WARNING: Failed to associate with bssid " . I have done every possible try to make it work but both of them does not work . At first , 1st one stopped working and i started using 2nd one . But after a month 2nd also stopped working . I thought there might be problem with my Linux (Backtrack 5 r3) . To sort it out i downloaded Kali Linux 2.0 but the problem didn't got solved . I also switched to another network with WPS on but still no luck .
Then an idea stuck into my mind to use Laptop's build-in adapter. This time i started reaver and to my charm , it worked fine .
So i also searched on internet related to this issue but i got no accurate results . And my both adapters are also useless for pin attempts . I think the issue is with the hardware somewhere .
If anyone can help a little with this issue , it will be really appreciated .... Thanks 4 Reading










